Shaijee and twest thanks for sharing their solutions using the /fs/ and /filerd/ rules. This exchange of ideas is valuable for everyone. I'd like to add some security information to help people make informed decisions.
About the /fs/ or /filerd/ rules
These solutions are quick and functional, especially in urgent situations. But it's important to understand what they mean.
Here's how the path works in the File Manager:
The typical structure is: /filerd/[UUID]/websites/[UUID]/fs/public_html%2Ffile
Important risks to consider: ⚠️
- Excessive breadth: They bypass any URL containing "/fs/" or "/filerd/". This includes sensitive files like .env, .htaccess, etc.
- You could lose protections. If all WAF (Web Application Firewall) rules are omitted, defenses against attacks such as SQLi/XSS, rate limiting, bot protection, etc., are exposed.
- Potential attack vectors: An attacker could exploit vulnerabilities in the File Manager (e.g., code injection if there's a vulnerable plugin).
- Loss of visibility: Cloudflare will stop logging events on these paths.
Optimized alternative – Recommended rule: ✅
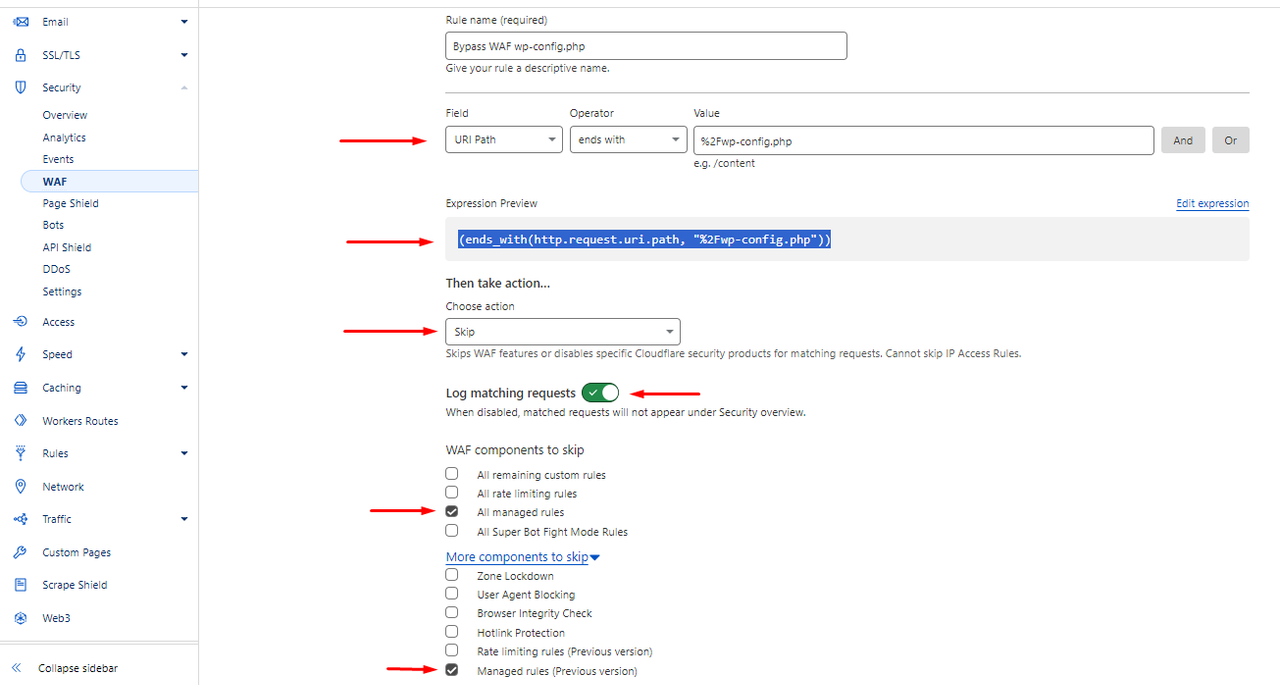
Field: URI Path > Operator: ends with > Value: %2Fwp-config.php
Expression Preview: (ends_with(http.request.uri.path, "%2Fwp-config.php"))
WAF components to omit:
🔹 ONLY:
- All managed rules
- Managed rules (Previous version)
Benefits:
- Pinpoint accuracy → Only affects wp-config.php.
- Maximum security → Keeps other protections active.
- Zero false positives → Does not interfere with other files.
- Avoids exposing additional files.
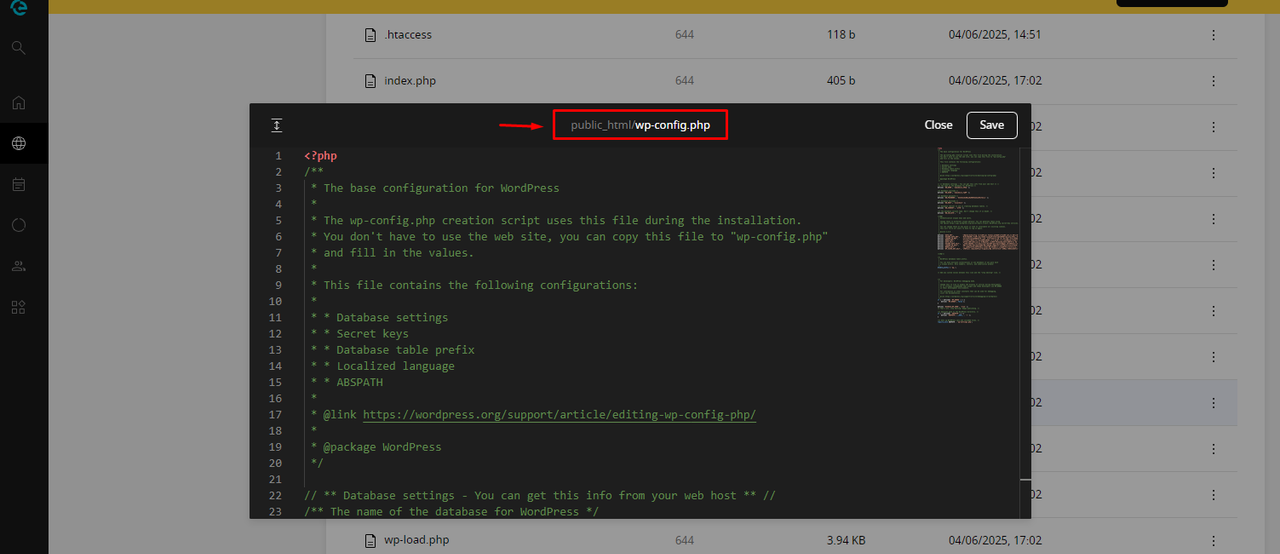
Here's an example of a bypass with the optimized rule, which lets you edit the wp-config file in the file manager:

📌 If you use broad rules (/fs/ or /filerd/):
To minimize risks, omit only:
- "All managed rules" + "Managed rules (Previous version)"
- Constantly monitor logs.
The ideal security balance is achieved by striking a balance between:
🔹 Functionality → Being able to edit what's necessary.
🔹 Protection → Not exposing other resources.
Best regards,
Omar.