cPFence UI is Here – Security Management, Now with a Mouse!
- Edited
Thanks for that. I agree with the hourly IPDB updates for sure. For the virus signatures I feel once a day would be fine if that saves like 80% of the incoming bandwidth every hour, but it's certainly not a big deal, especially since they don't take up extra space.
It's just that when looking out for issues/bugs due to the V12 updates, everything that's odd stands out suddenly, so that's why I asked.
- Edited
Version 3.3.37 (2nd March 2025)
Added
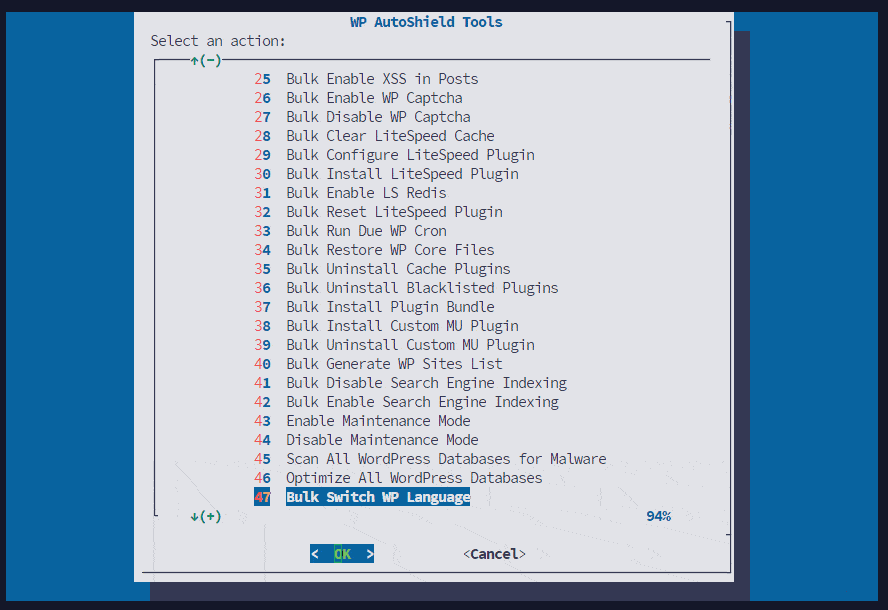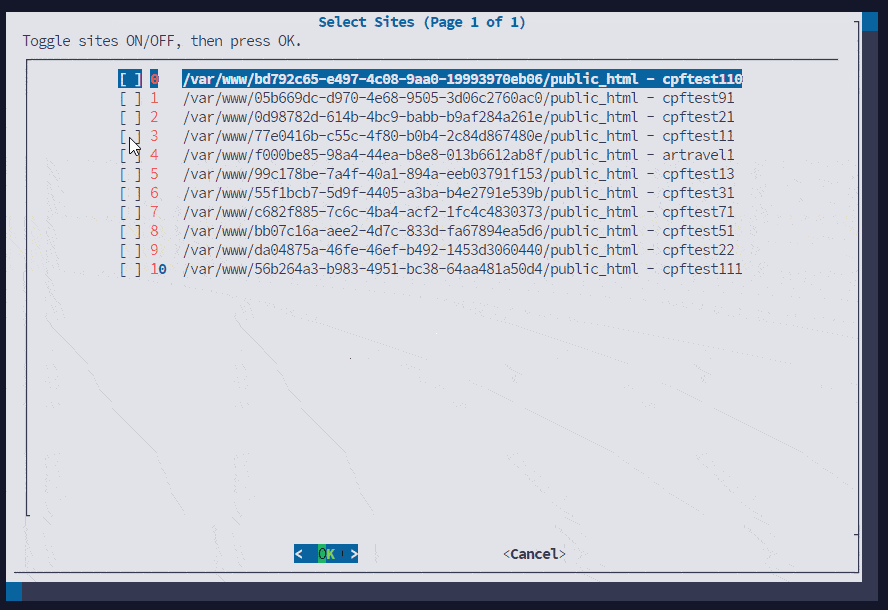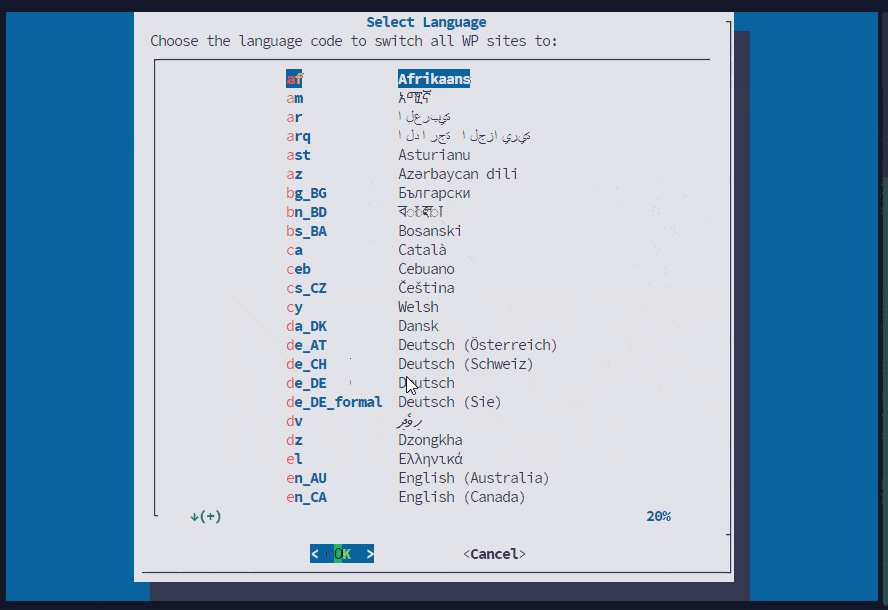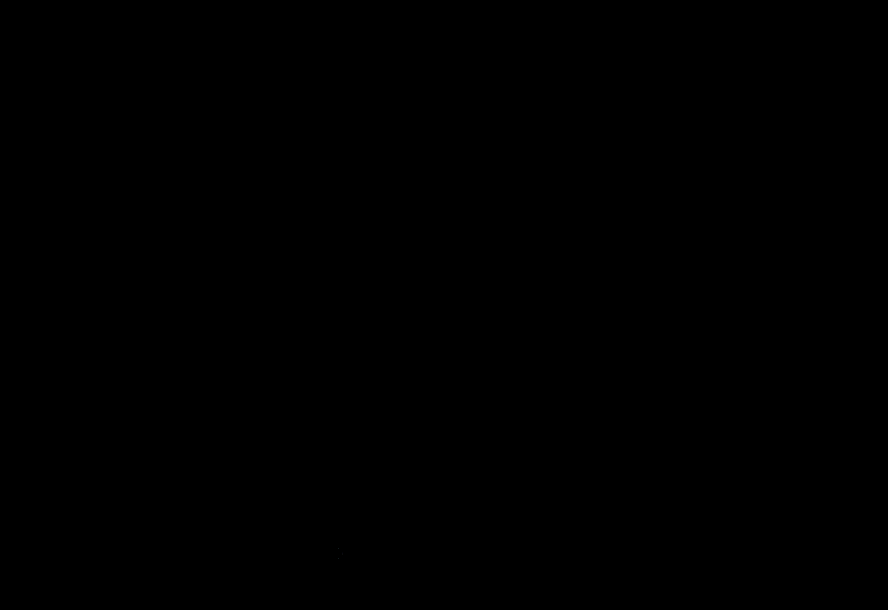
- Bulk Wordpress Language Change:
Now you can easily change the language of all or selected wordpress sites in bulk.
Improved
- Owl now monitors systemd for openlitespeed (ols) and litespeed (ls):
Owl will now ensure systemd remains in sync with the actual litespeed web server status, preventing unnecessary restarts. more details: enhance community discussion.
- Alerts will only be triggered if ols/ls web server fails to start.
- Waf Optimizations:
Additional compatibility improvements for various plugins and themes.
So I just discovered that I opened cpfence --ui on all of the servers in my cluster. Coincidently I lost internet for couple of mins and I lost connection to all of my terminal sessions. Then I left it as is. After few hours, I found that all of my servers are showing a high CPU usage. When I ran the top command, I found a process with command "dialog" running on all servers is consuming 100% CPU. Is it cpfence UI? Because none of my servers are having anything related to dialog on it. @cPFence
The UI CPU usage is usually close to zero. Please open a ticket so we can check it out for you.
MDG There's already a bulk plugin install option!
cpfence --bulk-install-wp-plugin
bluelinq-computers basically intalling via plugin zips.
Yes, you can already bulk install a plugin by searching for the plugin slug, using a URL with the plugin zip file, or specifying a path on the server with the plugin zip file.
Version 3.3.39 (7th March 2025)
Improved
- Enhanced the Admin UI to better handle scenarios where users get disconnected or close the terminal with no clean exit, ensuring improved performance and stability during sessions.
Thanks to those who requested it. We’ve just updated our blog post with the full list for v12. Hope it helps:
Essential Daily Commands for Managing Your Enhance Server (updated for v12)
Version 3.3.40 (9th March 2025)
Added
- Inode Usage Monitoring:
cPFence Owl now tracks filesystem inode usage in real-time, ensuring early detection of excessive file creation, potential abuse, or misconfigurations that could impact system stability and security. High inode usage can lead to server instability, failed writes, and performance issues—this new monitoring feature helps prevent these risks before they cause serious problems.
- New Interactive Tool for Real-Time WAF Log Tracking:
Quickly identify and troubleshoot potential false positives in cPFence WAF logs with this new interactive tool. This tool:
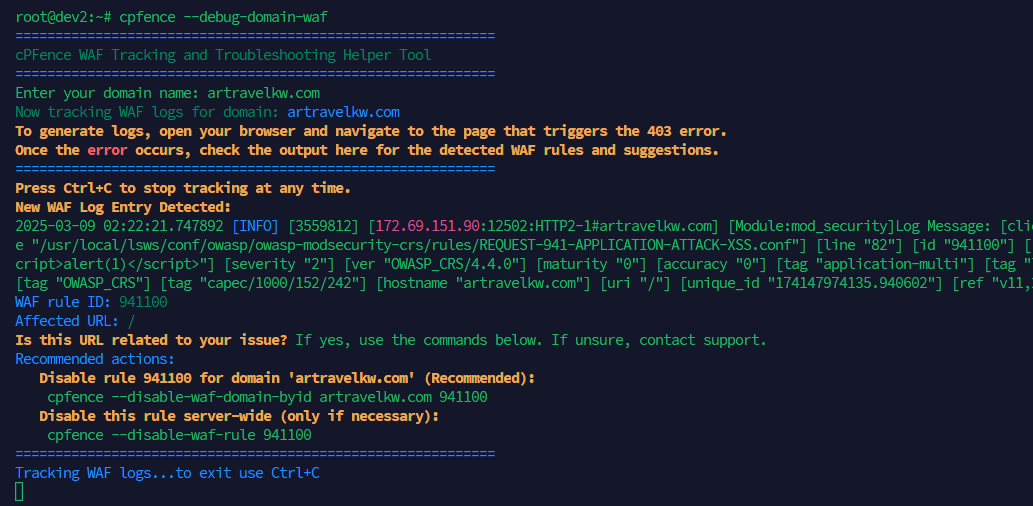
Automatically detects rule numbers responsible for blocked requests.
Suggests ready-to-use whitelisting commands for immediate action.
Run the tool using:
cpfence --debug-domain-waf
Improved
- Enhanced WP-AutoShield compatibility with Bedrock-based WordPress installations.
- Optimized WAF rules to prevent conflicts with phpMyAdmin on Enhance v12.
Enhanced WP-AutoShield compatibility with Bedrock-based WordPress installations.
This was nice to see. Do you guys personally use Bedrock on any of your installs?
Version 3.3.41 (11th March 2025)
Added
- ASN Blocking – A First in Server Security!
cPFence is now the first security product to offer ASN blocking for both IPv4 and IPv6, bringing unmatched flexibility to Enhance users.
Blocking entire ASN ranges is a powerful defense mechanism, especially during large-scale DDoS attacks.
cpfence --blacklist-asn→ Instantly block an entire ASN range to neutralize threats.
- New Under Attack Mode (Beta) – Rapid DDoS Defense:
cPFence now features an Under Attack Mode designed to apply stricter and faster DDoS defenses when an attack is detected. This mode ensures enhanced protection against high-volume attacks while maintaining server stability.
cpfence --under-attack-on→ Activates aggressive protections against ongoing DDoS attacks.cpfence --under-attack-off→ Restores recommended security settings once the attack is over.
cPFence This is amazing. I ran into an issue a little while ago and reached out to my then security provider about ASN block, but they were not able to offer it at the time. Great job on this. Also, would it be possible to include an email notification when an IP is temporarily or permanently blocked due to DDOS or connection issues? Maybe this could be an option we can toggle on or off. It could help to keep track of which ASN or IPs might be sending too many connections, and nice to stay aware when something like this happens.
